API (Self-hosted on AWS): Setup Guide
Are you looking for the SaaS offering?
Deploying the attachmentAV API to your AWS account is simple and takes about 15 minutes.
First, open attachmentAV Virus and Malware Scan API in the AWS Marketplace and click the View purchase options button.
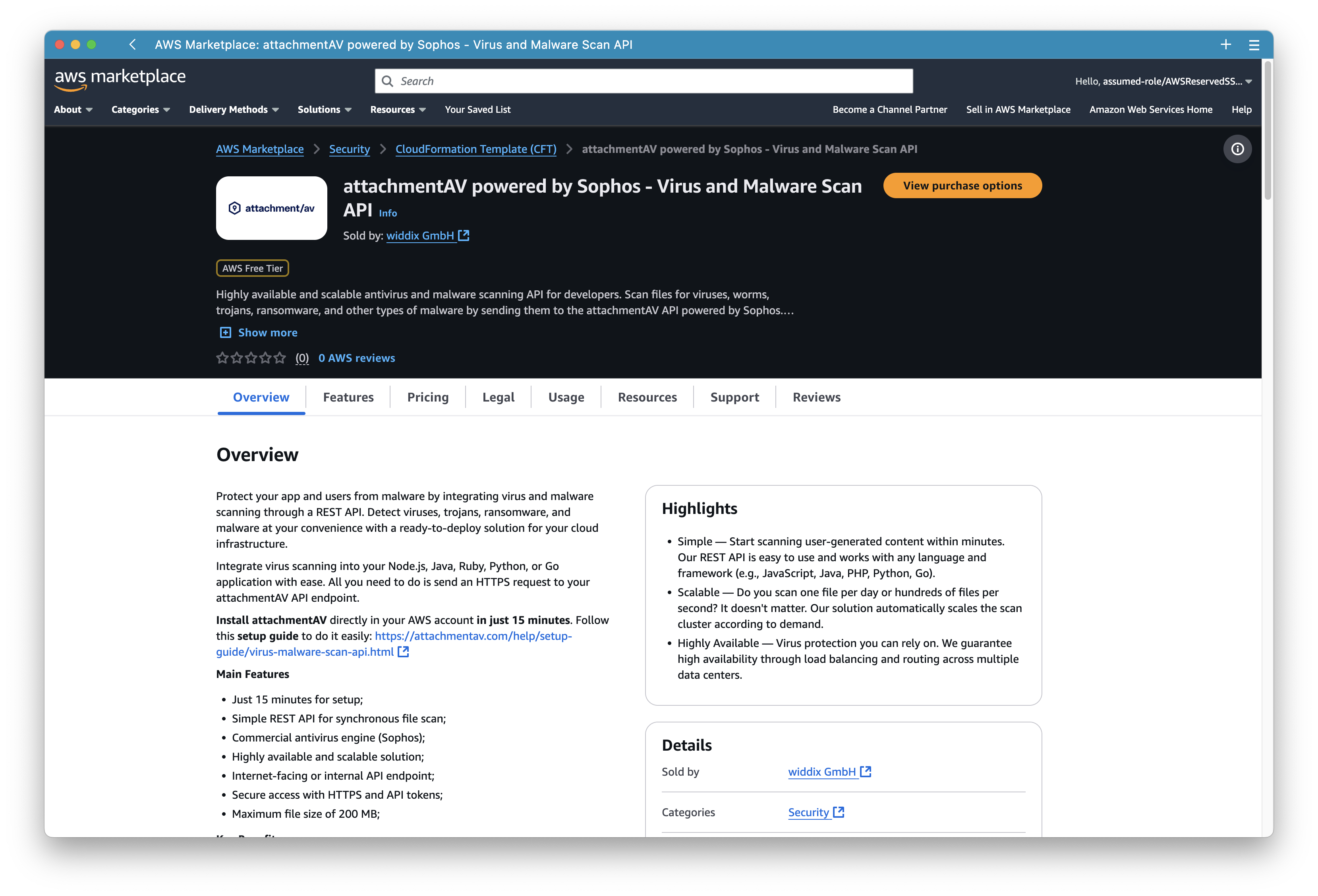
Next, review the offer …
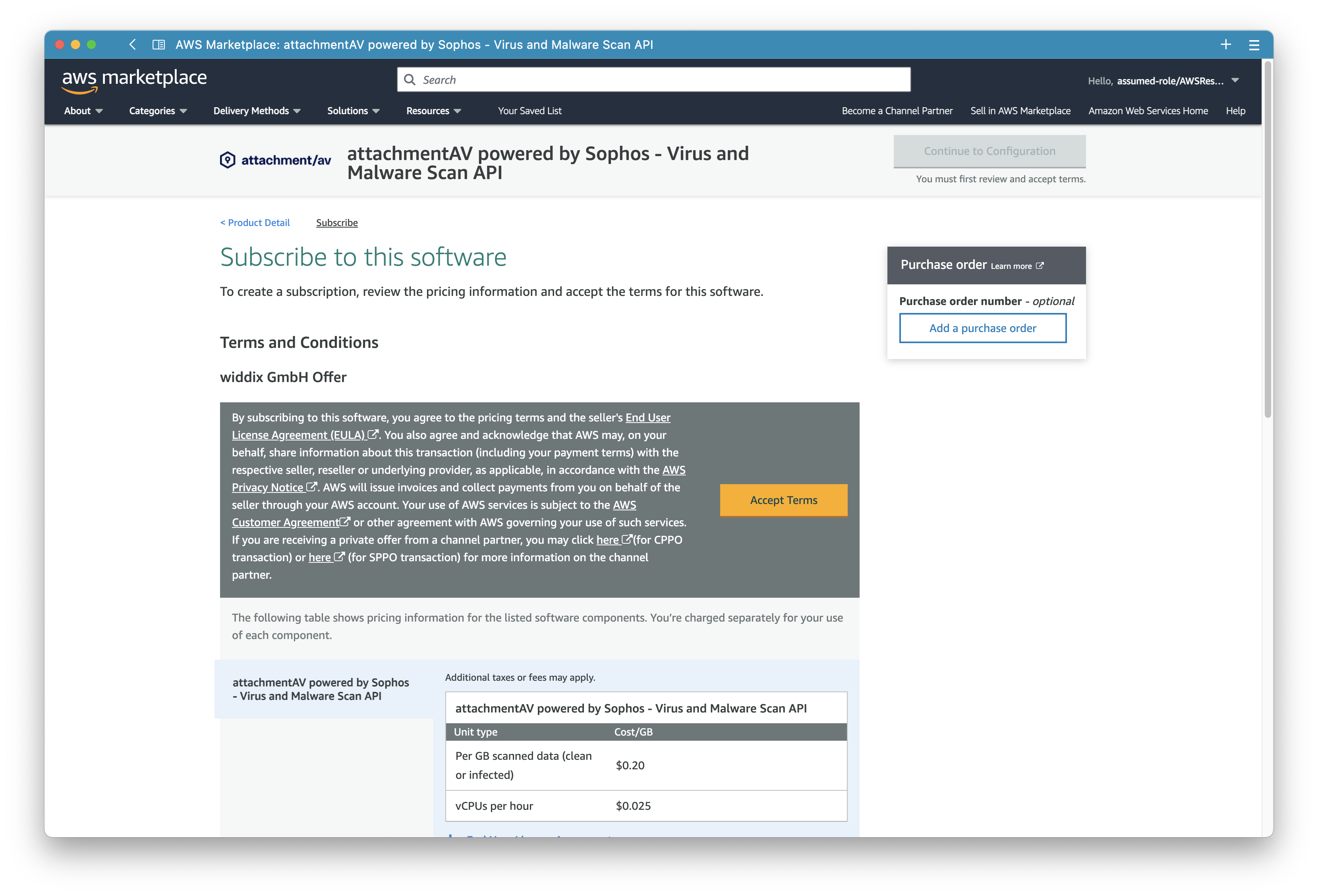
… and press the Subscribe button at the bottom of th page.
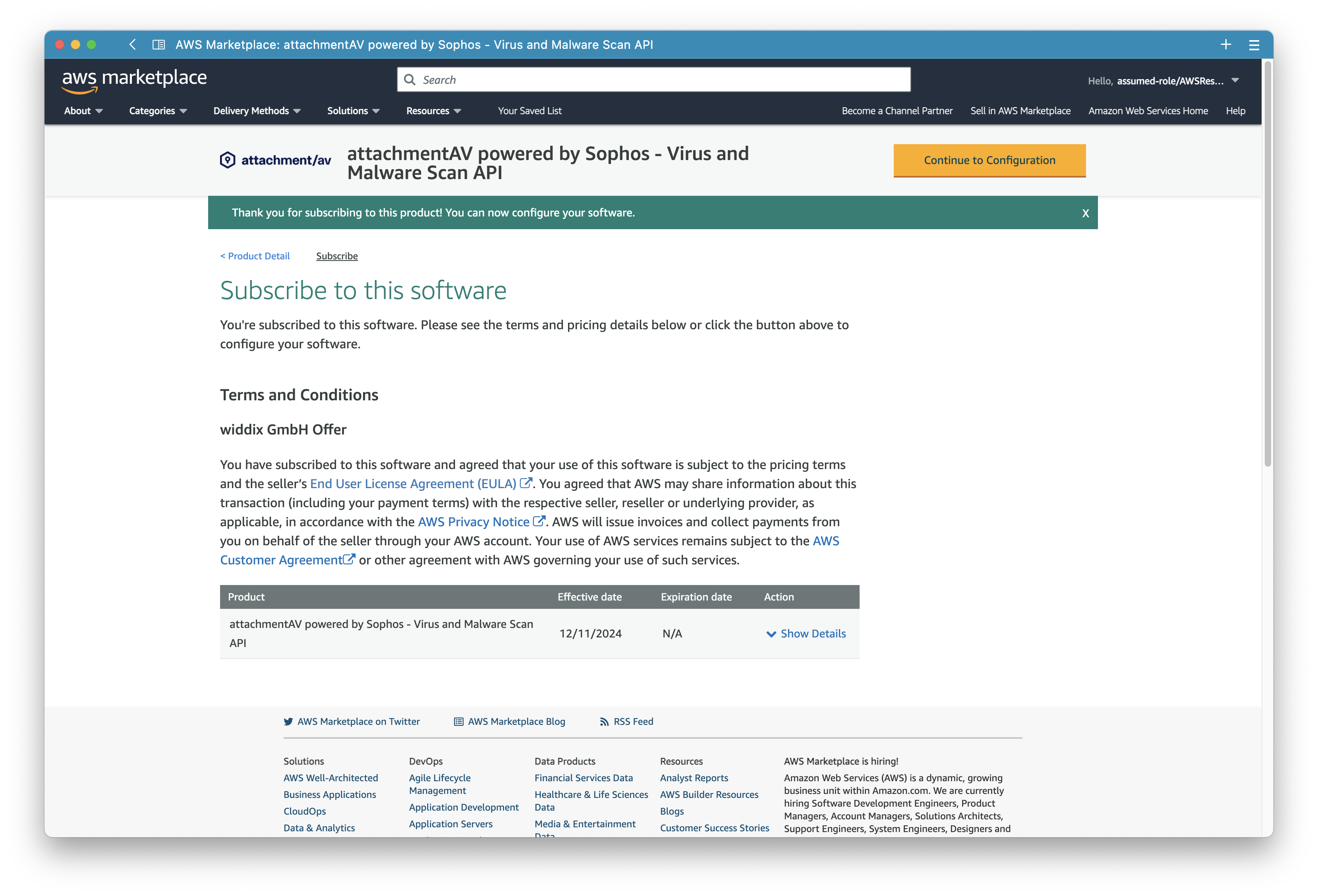
It takes a few minutes until AWS processes the subscription.
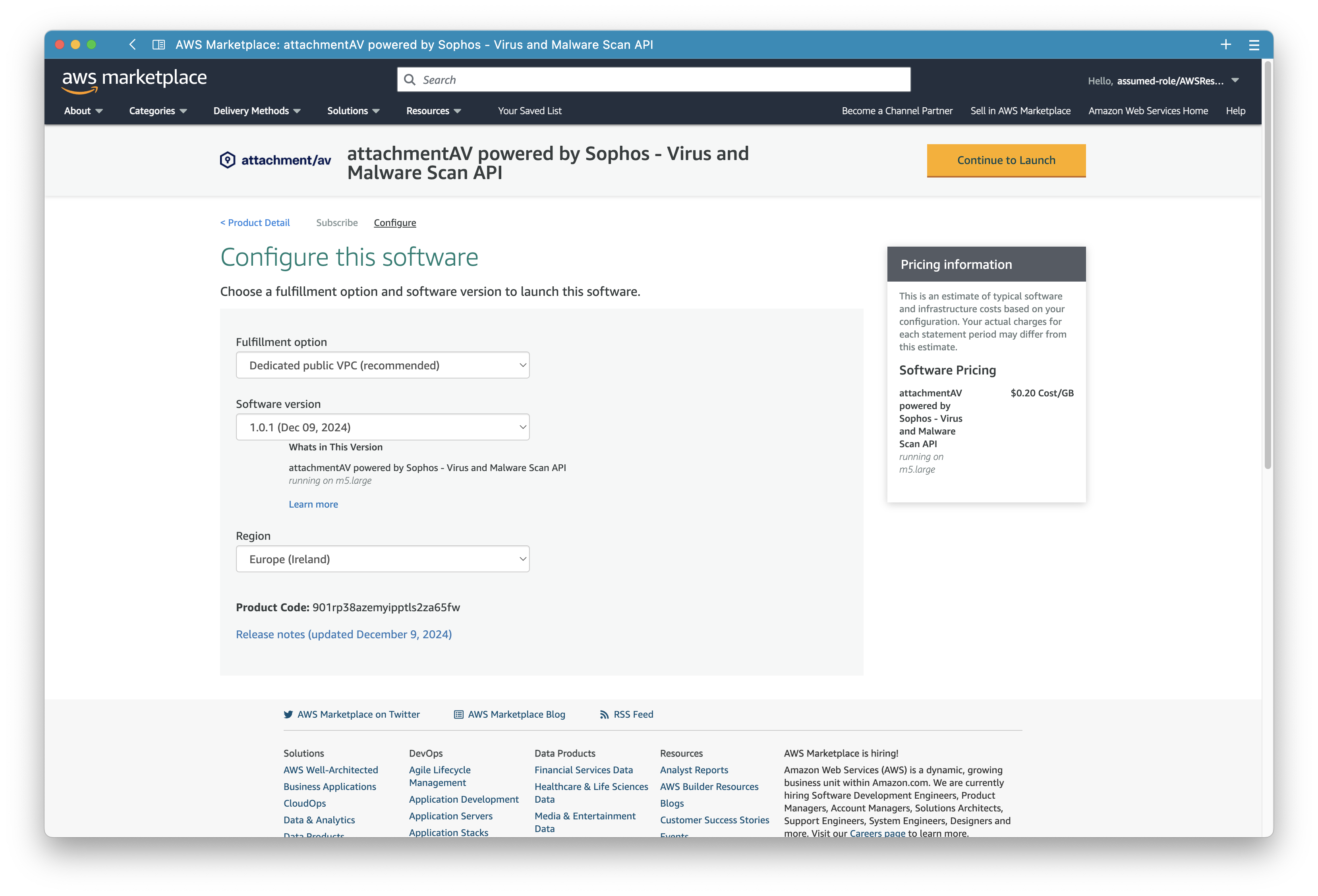
After successfully purchasing attachmentAV, proceed by clicking the Launch software button.
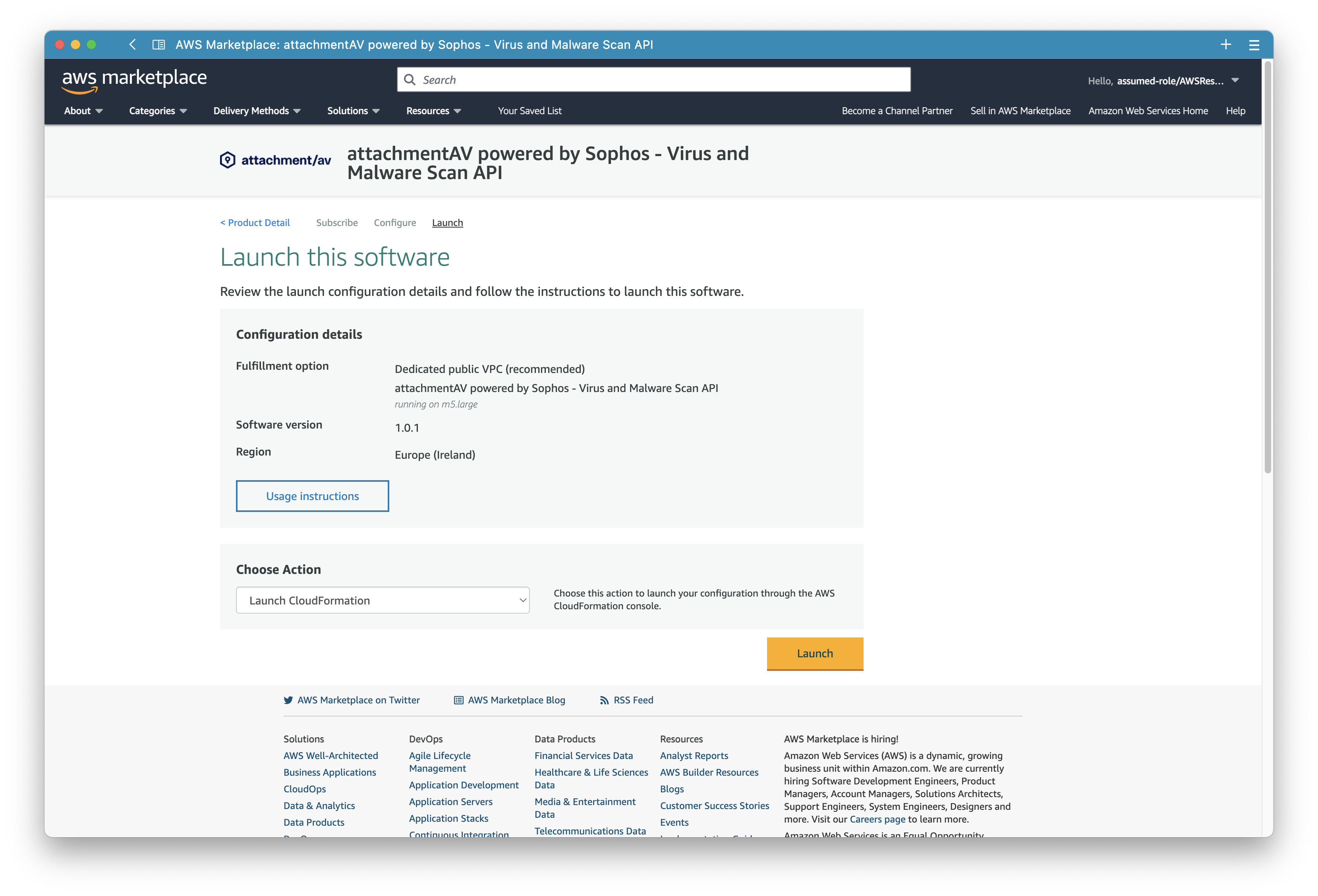
Next, prepare the launch if attachmentAV.
First, select the latest available version.
Second, choose a CloudFormation template. We provide two deployment options.
Dedicated public VPC (recommended)deploys a separate VPC in your AWS account. The VPC is pre-configured for attachmentAV API and ensures to isolate the workload from other workloads in the same account. This option deploys an Internet-facing API and uses firewall rules as well as an authentication token to secure the workload.Dedicated private VPCdeploys a separate VPC in your AWS account with no connection to the Internet. The VPC is pre-configured for attachmentAV API and ensures to isolate the workload from other workloads in the same account. This option deploys an internal API and uses firewall rules as well as an authentication token to secure the workload.Existing VPCallows you to deploy the attachmentAV API into an existing VPC. There are two main reasons for choosing this option: a) you want to deploy an internal API, or b) you have very specific networking requirements to fulfill security governance standards. Read the Existing VPC Network Guide to prepare your VPC configuration.
Third, pick an AWS region.
Continue by clicking the Launch with CloudFormation button.
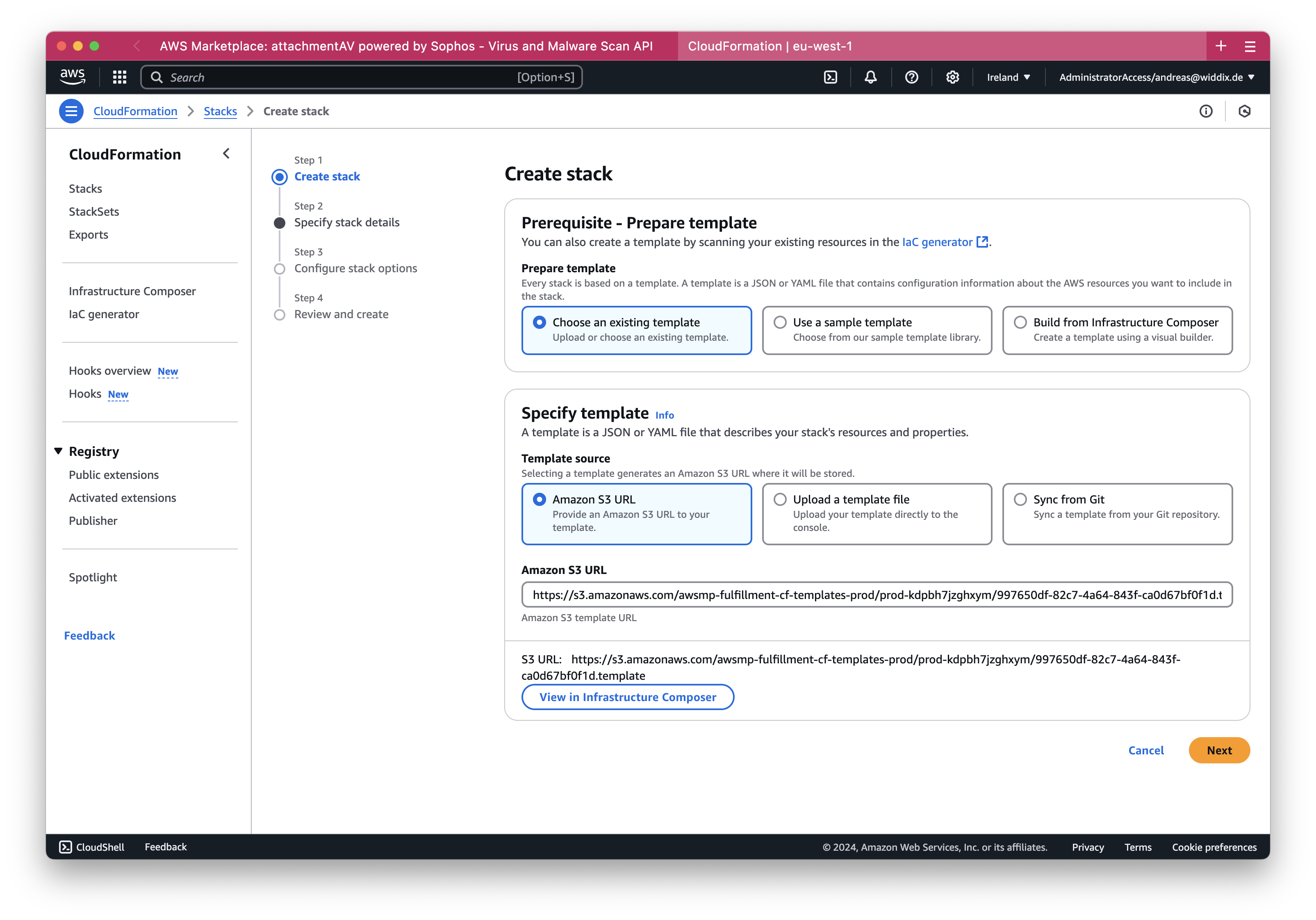
You are getting redirected to CloudFormation. Keep the defaults in the first page of the wizard and continue by clicking the Next button.
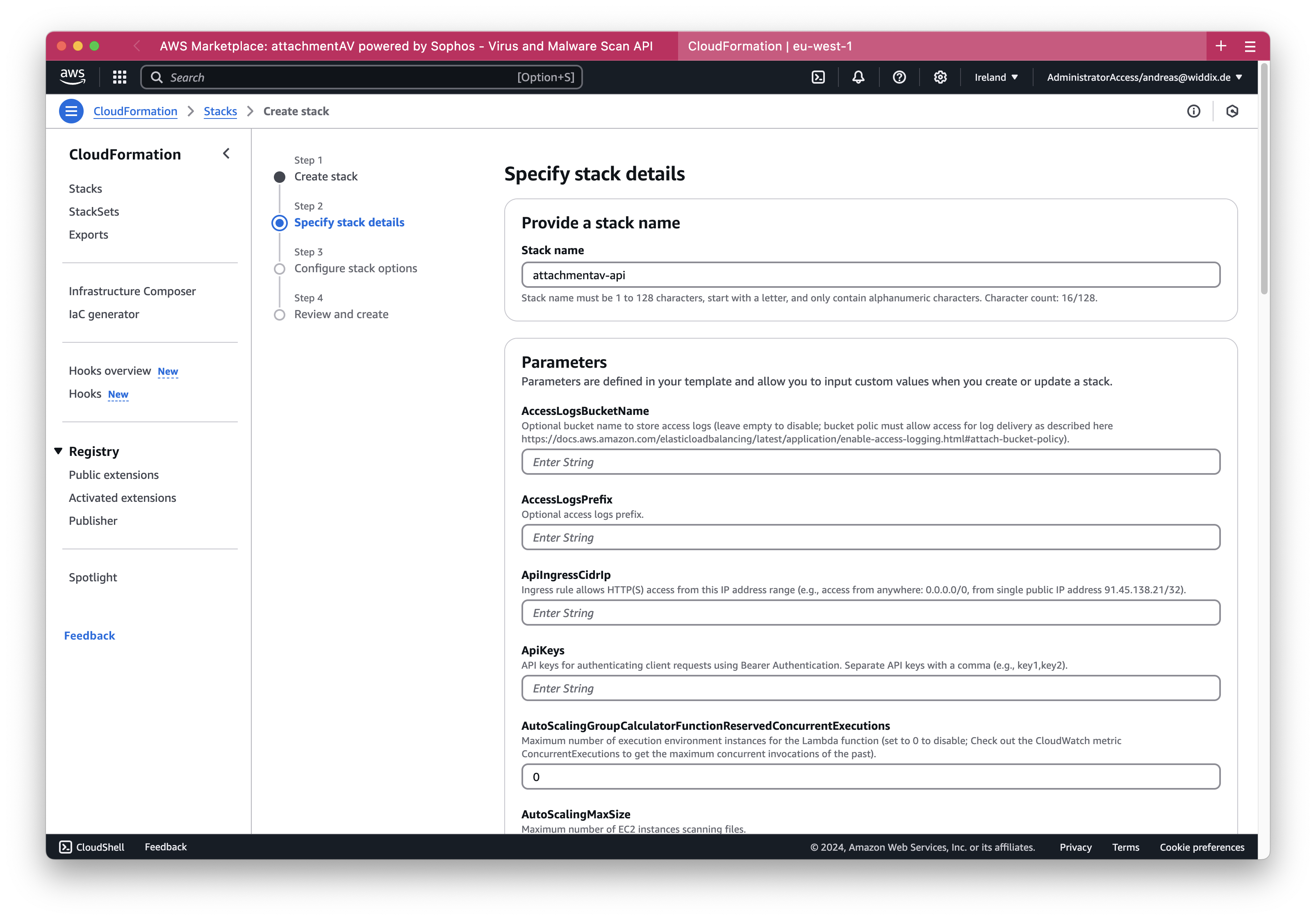
Now, it is time to configure the attachmentAV API for your needs. The following parameters are mandatory:
ApiKeys: API keys for authenticating client requests using Bearer Authentication. Separate API keys with a comma (e.g., key1,key2).KeyName: Name of the EC2 key pair to log in via SSH (username: ec2-user).ApiIngressCidrIp: Ingress rule allows HTTP(S) access from this IP address range (e.g., access from anywhere: 0.0.0.0/0, from single public IP address 91.45.138.21/32).
attachmentAV API supports two types of DNS and certificate configuration. Choose by selecting one of the following options for the DnsConfiguration parameter.
AUTO_ROUTE_53- Automatically configure DNS and the certificate. Works for Internet-facing API endpoints only.MANUAL- Configure DNS and the certificate manually. Works for both Internet-facing and internal API endpoints.
When selecting AUTO_ROUTE_53 the following additional parameters are required:
HostedZoneId: Route 53 public hosted zone ID.DomainName: Domain name added to Route 53 public hosted zone and Certificate Manager public certificate.
Alternatively, if you choose MANUAL the following additional parameters are required:
CertificateArn: ACM public certificate ARN (required if DnsConfiguration:=MANUAL).
After you have configured all the parameters, click the Next button.
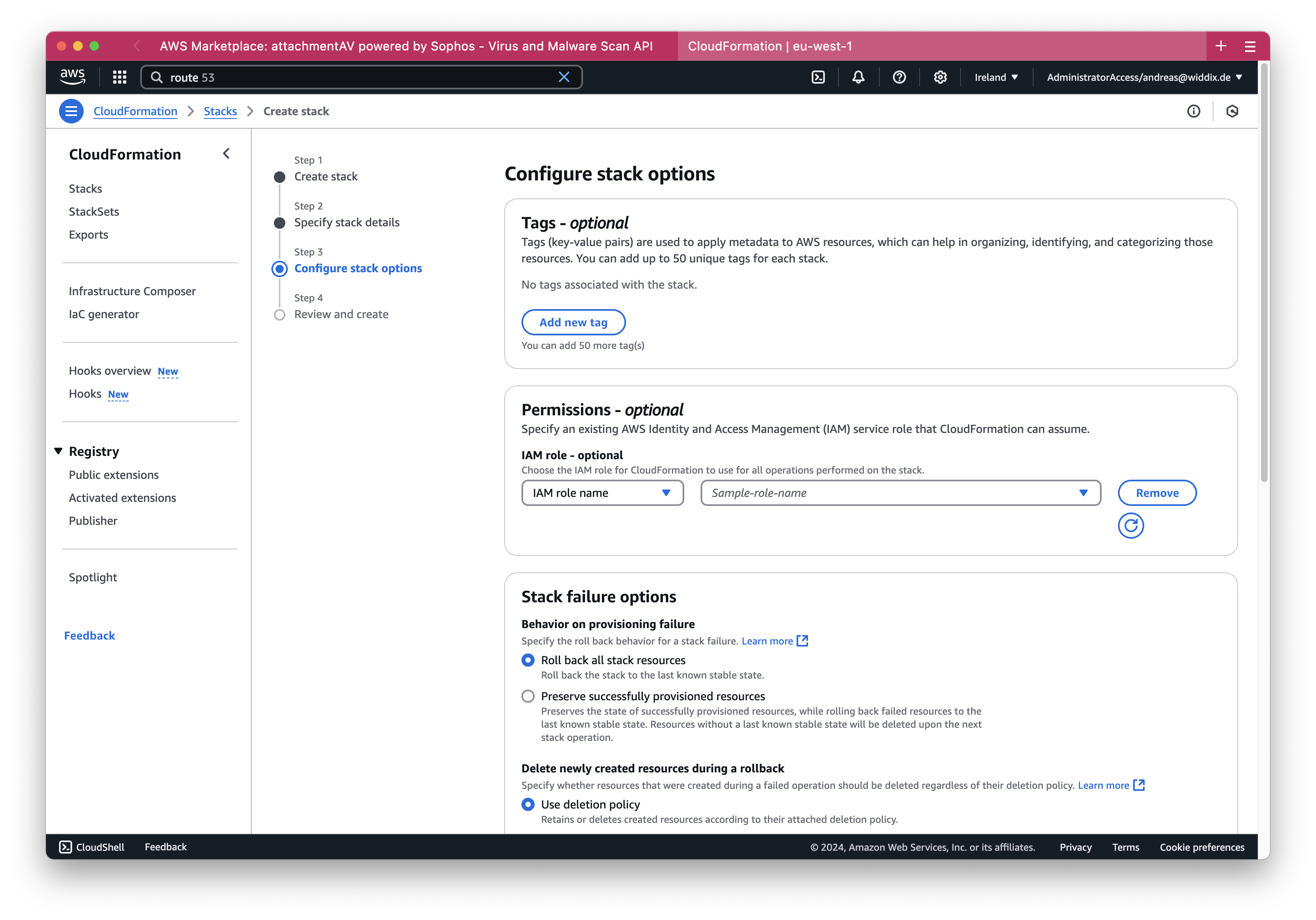
In the next step, scroll to the bottom …
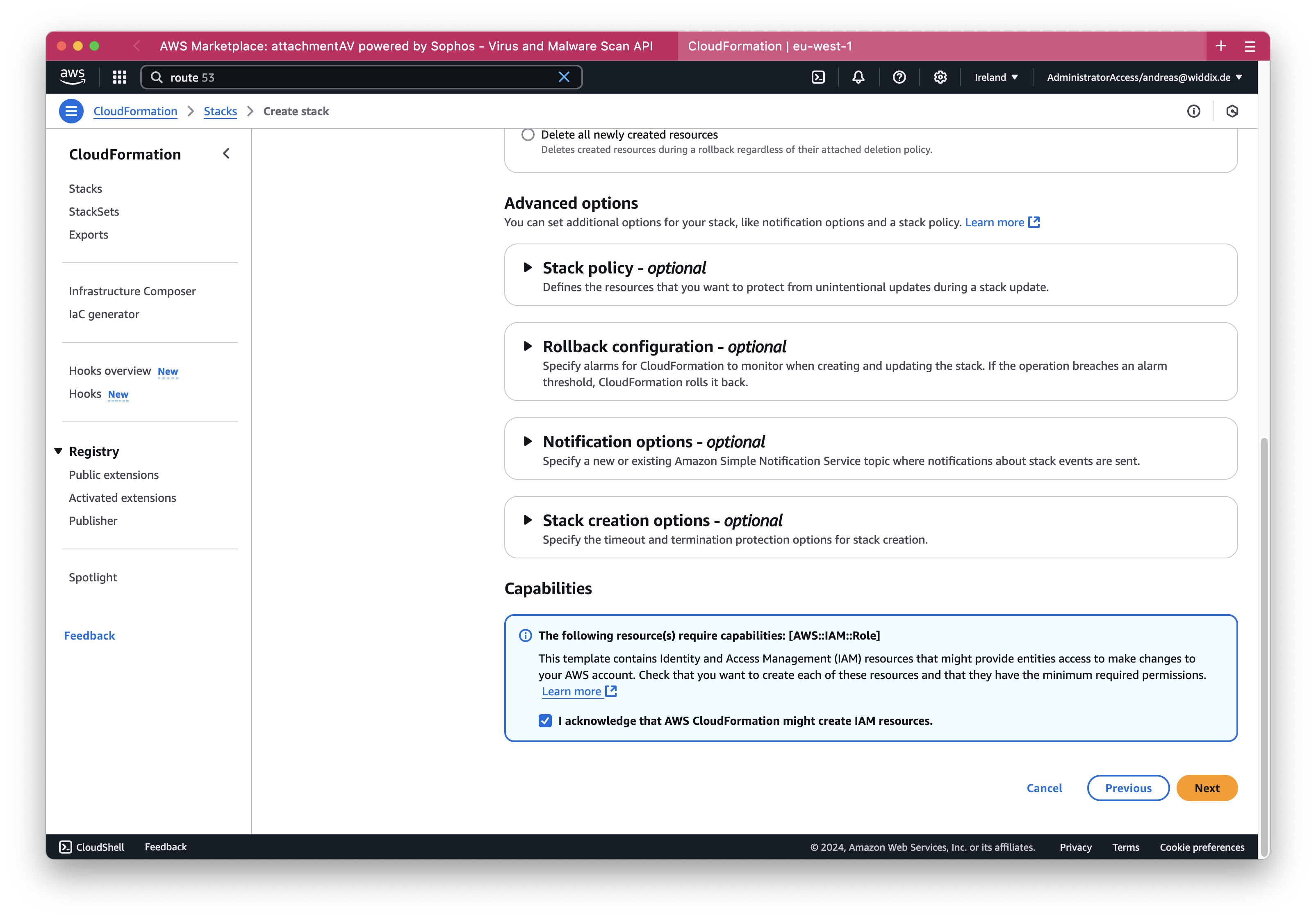
… and check the I acknowledge that AWS CloudFormation might create IAM resource box. Then, press the Next button.
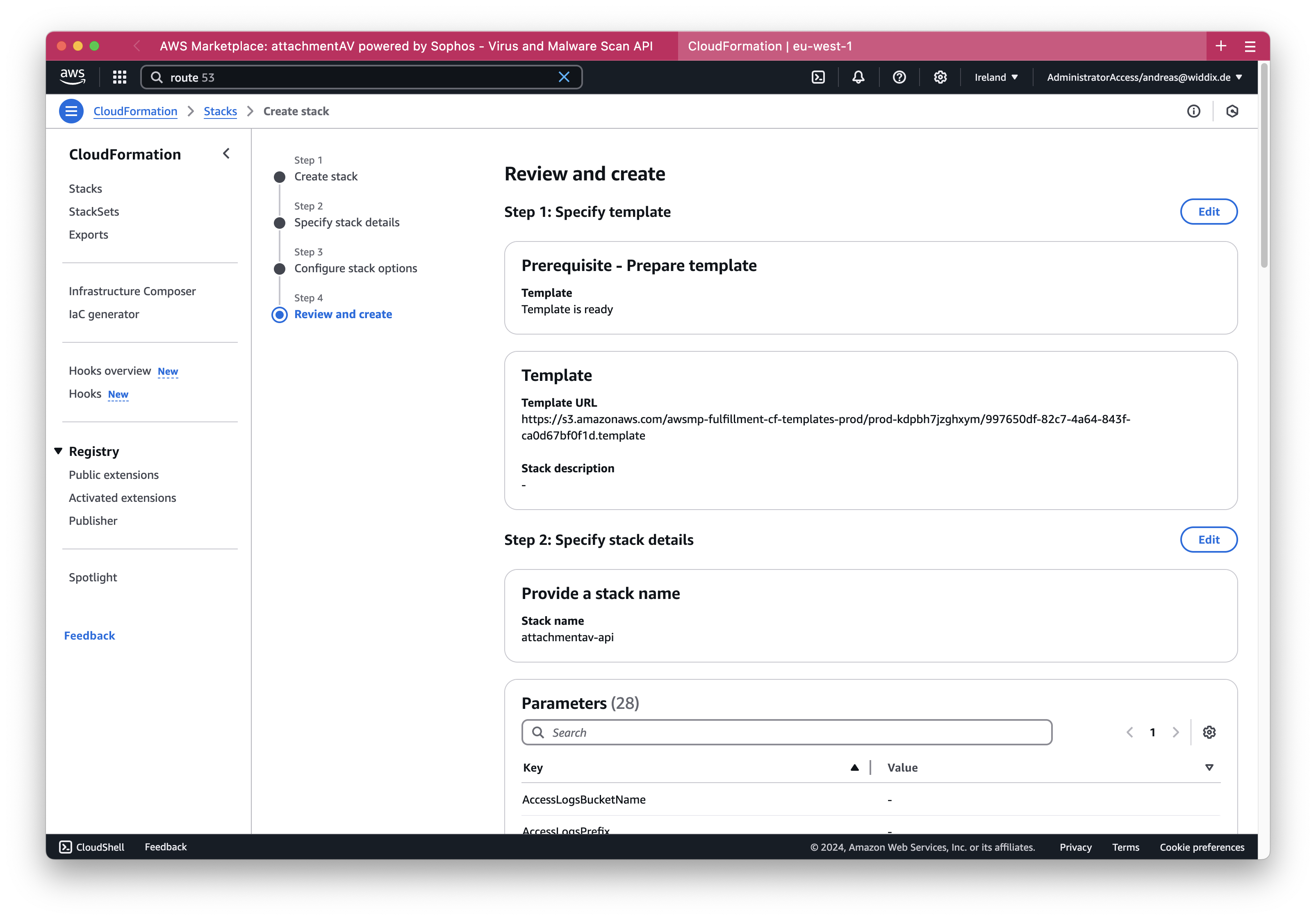
Next, review the configuration of the CloudFormation stack and click the Submit button at the bottom of the page.
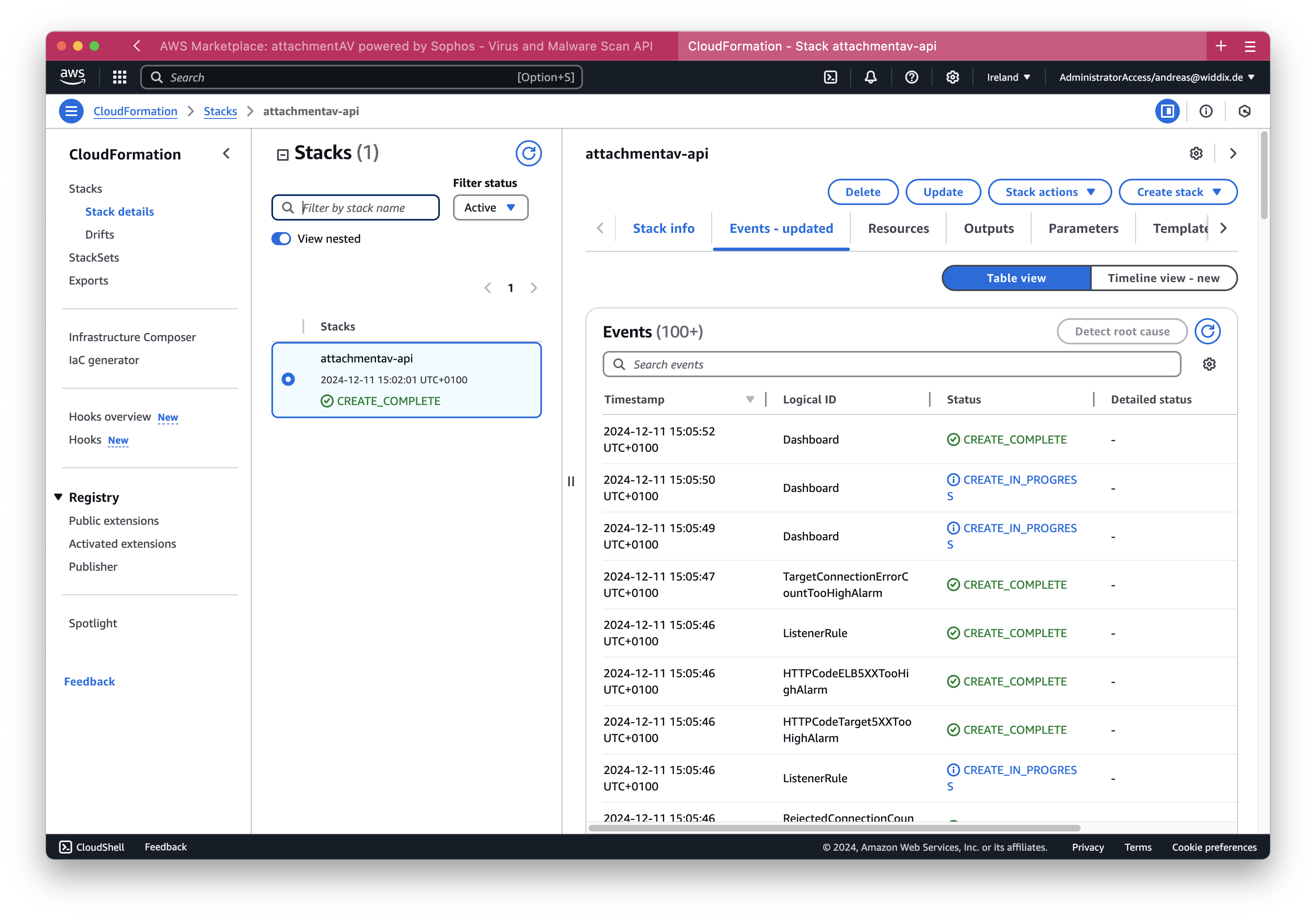
It will take about five minutes until the CloudFormation stack reaches the state CREATE_COMPLETE.
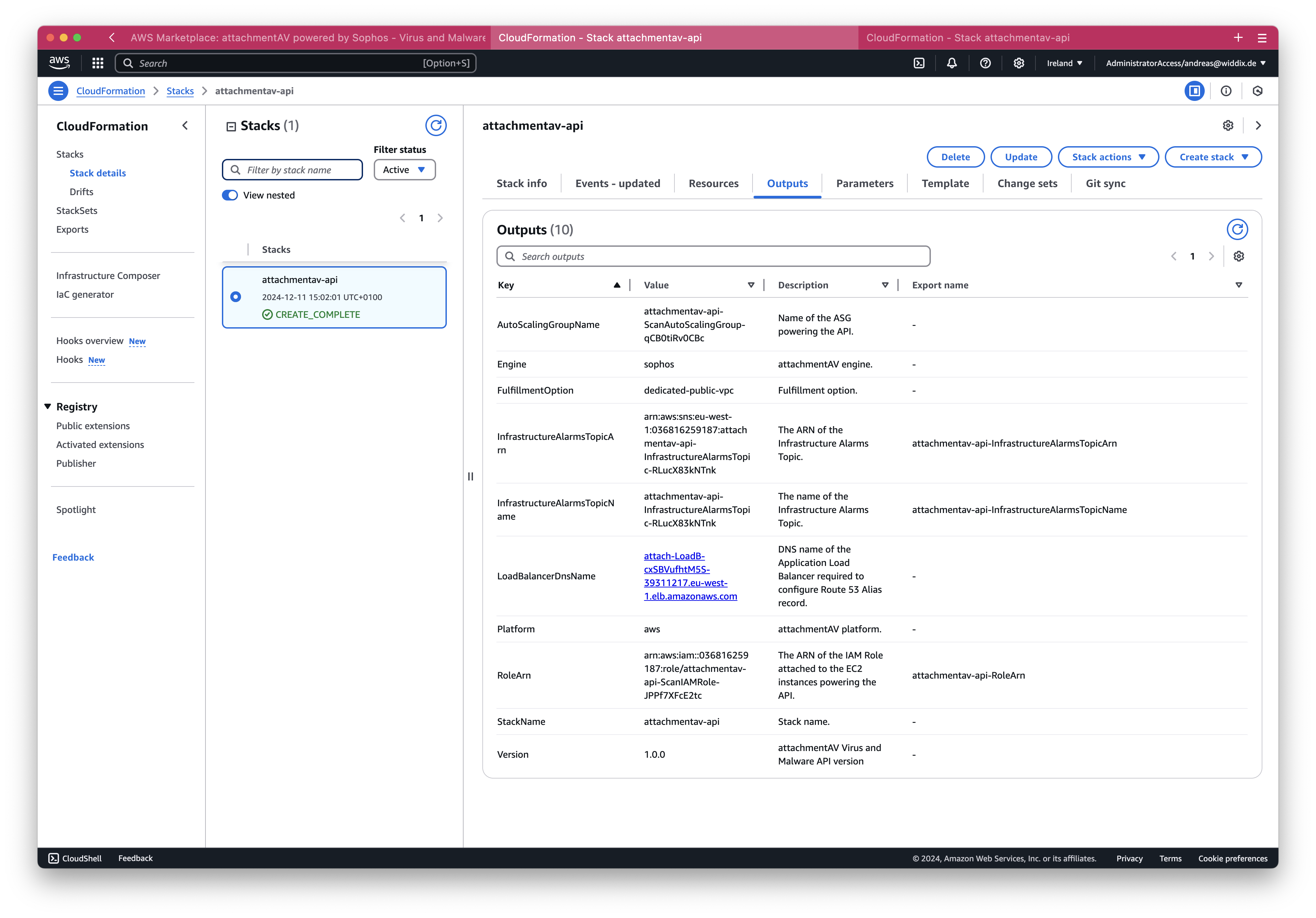
Lucky you, if you selected AUTO_ROUTE_53 as DnsConfiguration: you are done! The attachmentAV API is reachable under the DNS name you configured with the DomainName parameter. Continue to send requests to your attachmentAV API.
In case you selected MANUAL as DnsConfiguration you need to find out the DNS name of the load balancer next. Select the Outputs tab of the CloudFormation stack. There you will find an output named LoadBalancerDnsName, which is attach-LoadB-cxSBVufhtM5S-39311217.eu-west-1.elb.amazonaws.com in our example. Ensure to create a CNAME record pointing to the value of LoadBalancerDnsName. The attachmentAV API is reachable under the DNS name of the CNAME you created. Continue to send requests to your attachmentAV API.

Uninstall (#)
- Visit the AWS CloudFormation Console.
- Ensure that you are in the correct region.
- Navigate to Stacks.
- Click on the attachmentAV stack (if you followed the docs, the name is
attachmentav). - At the top right, click on Delete.
After deleting the stack, you can cancel your AWS Marketplace subscription:
- Visit the AWS Marketplace Console.
- Click on the attachmentAV subscription.
- Click on Actions and Cancel subscription.